
In part one of this three-part series on privacy, I walked through the changing privacy landscape and the various risks worth considering. In this installment, I’ll explore methodologies and tactics I recommend using to reduce those risks.
Let’s jump right in!
Ask yourself who is to be trusted
It is easy to be cynical, but not every government and company is created equal. Each government maintains a unique scope of diplomacy and influence. Meanwhile, some companies have strong stances on privacy through both word and action, while others are on the opposite end of that spectrum. Whenever possible, use this knowledge to advise your decisions.
Some convenient rules of thumb:
Western governments
They tend to share values and therefore intelligence. For this reason, the jurisdiction of the services you use and where their data is transmitted and stored is highly relevant.
Business models
Companies that make most of their money by selling ads and intelligence will generally work counter to your privacy goals. Think Google (which owns Waze, Android, etc) and Facebook (which owns Instagram, WhatsApp, etc). Meanwhile, companies that make most of their money in a more traditional fashion - by selling products and services directly to consumers for unsubsidized prices - will generally work to maintain your privacy. Think Apple and Microsoft.
Exceptions
Notice how some products, like Android phones, may at first seem benign because they are being sold to consumers for hefty price tags. But Android is strategically owned by Google, which means the Android phones themselves work to serve Google’s data collection and advertising business, even when Google isn’t the entity manufacturing the phones.
Then there are companies like Macy’s and many other retailers which have very traditional business models, but still engage heavily in online advertising including uploading data they collect about you to their advertising platforms.
It’s always important to understand the basics of why a business exists and how it operates before deciding how much you trust it.
Limit your public content
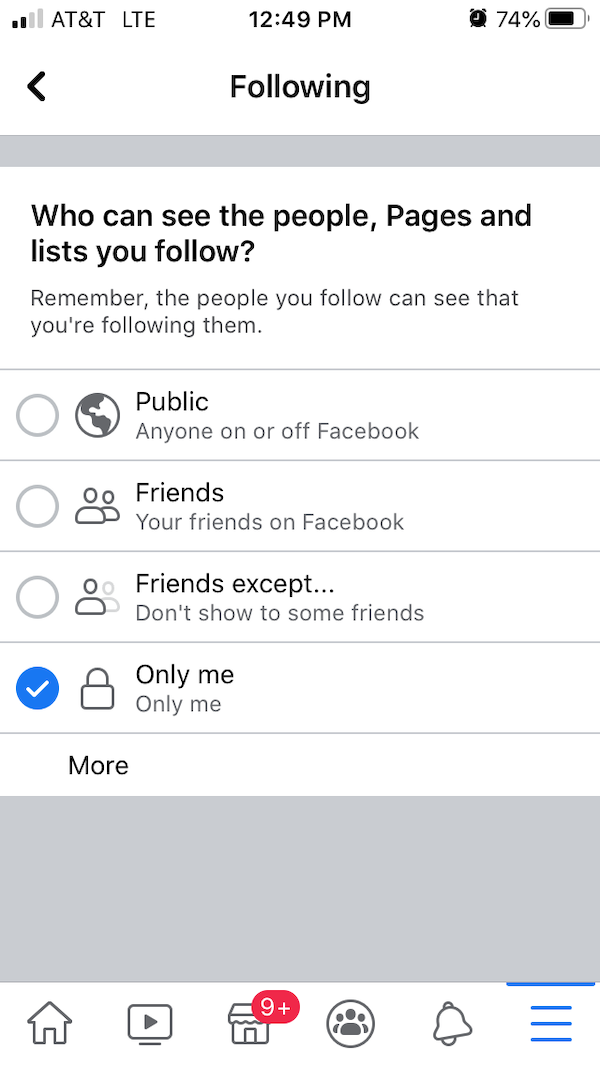 Make sure you know for sure which content you publish is public vs. private. Most social media platforms have features that overexpose the content you post and actions you take by default. This can result in strangers and loose connections getting more insight into your life than you ever intended. It is on you to learn about the platforms you use and check their privacy settings to ensure they’re configured according to your wishes.
Make sure you know for sure which content you publish is public vs. private. Most social media platforms have features that overexpose the content you post and actions you take by default. This can result in strangers and loose connections getting more insight into your life than you ever intended. It is on you to learn about the platforms you use and check their privacy settings to ensure they’re configured according to your wishes.
Even then, tread carefully when posting any content that you you believe is safe for public consumption, but has the potential to overexpose you when combined with other content. For example, you may never want to reveal your street address to the general public, but it can inadvertently happen if in one post you include a photo of a chain storefront that is across the street from your house and on your Facebook page you reveal what town you live in. Neither in a vacuum would reveal your home address, but the two together could be used to pinpoint it.
Disable ad targeting
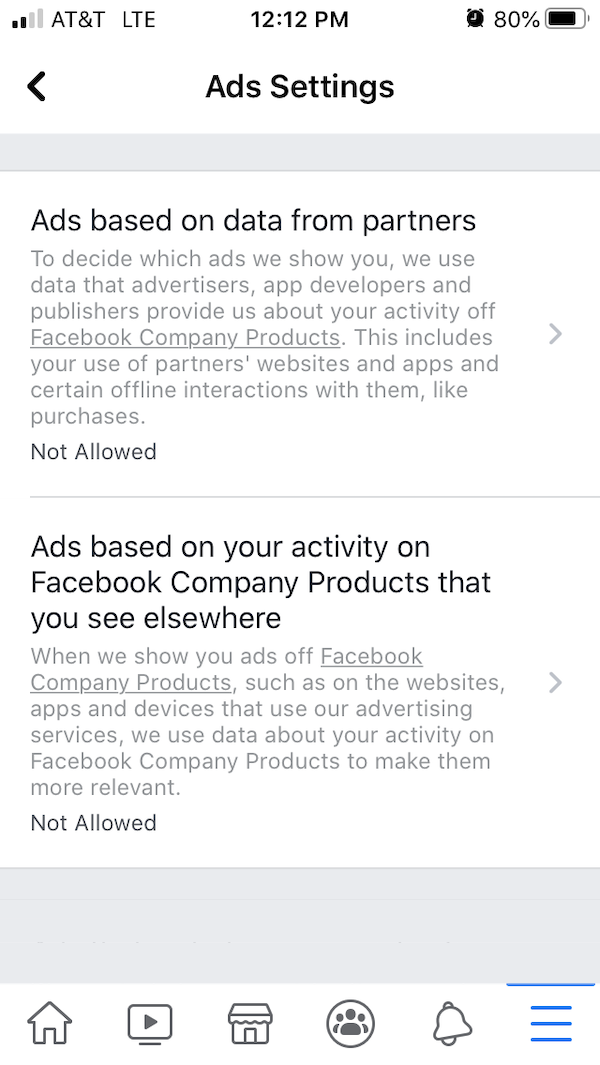 Most platforms use the content you post and the actions you take online, by default, to feed you highly targeted advertising. This doesn’t need to happen. In many of these platforms, you can change your advertising preferences so that targeting is significantly less aggressive. Do that.
Most platforms use the content you post and the actions you take online, by default, to feed you highly targeted advertising. This doesn’t need to happen. In many of these platforms, you can change your advertising preferences so that targeting is significantly less aggressive. Do that.
Limit data collection
You often have control over the data you share with services.
Location
It’s true that in some cases, you simply have to share your location with a service. For example, if you want to use Google Maps on your phone, Google is going to have to know your location while you use the app. That said, many websites and apps ask for your location as a matter of convenience, or worse, total exploitation. And they ask for it more often than they need.
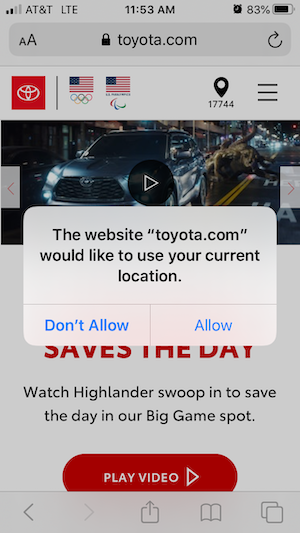 Next time you visit a car manufacturer’s website, ask yourself, “does this manufacturer really need to know exactly where I am right now?” They ask you this so they can find the nearest dealer (and of course, collect your private data). But you could simply enter your zip code to find the dealership closest to you without revealing exactly where you live.
Next time you visit a car manufacturer’s website, ask yourself, “does this manufacturer really need to know exactly where I am right now?” They ask you this so they can find the nearest dealer (and of course, collect your private data). But you could simply enter your zip code to find the dealership closest to you without revealing exactly where you live.
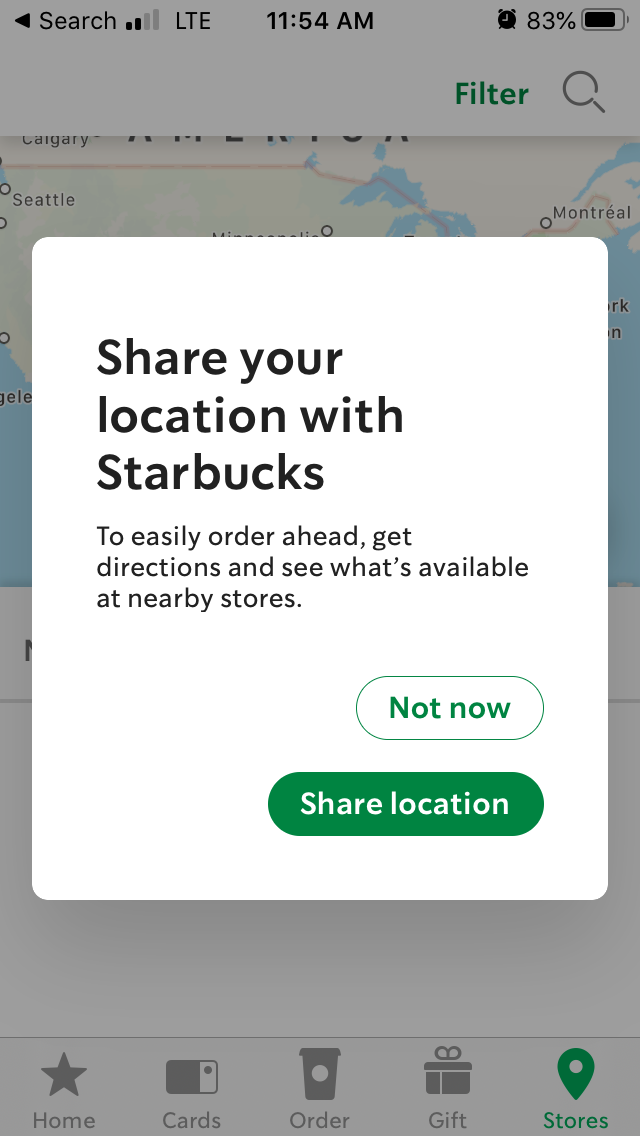 Next time you download a rewards app, ask yourself, “does this coffee chain really need to track exactly where I am all of the time?” They ask this of you so that they can push local promotions to you and help you more easily find local stores to order from once in the app. But you can find the nearest store and also all of its promotions by simply opening the app and entering in a zip code.
Next time you download a rewards app, ask yourself, “does this coffee chain really need to track exactly where I am all of the time?” They ask this of you so that they can push local promotions to you and help you more easily find local stores to order from once in the app. But you can find the nearest store and also all of its promotions by simply opening the app and entering in a zip code.
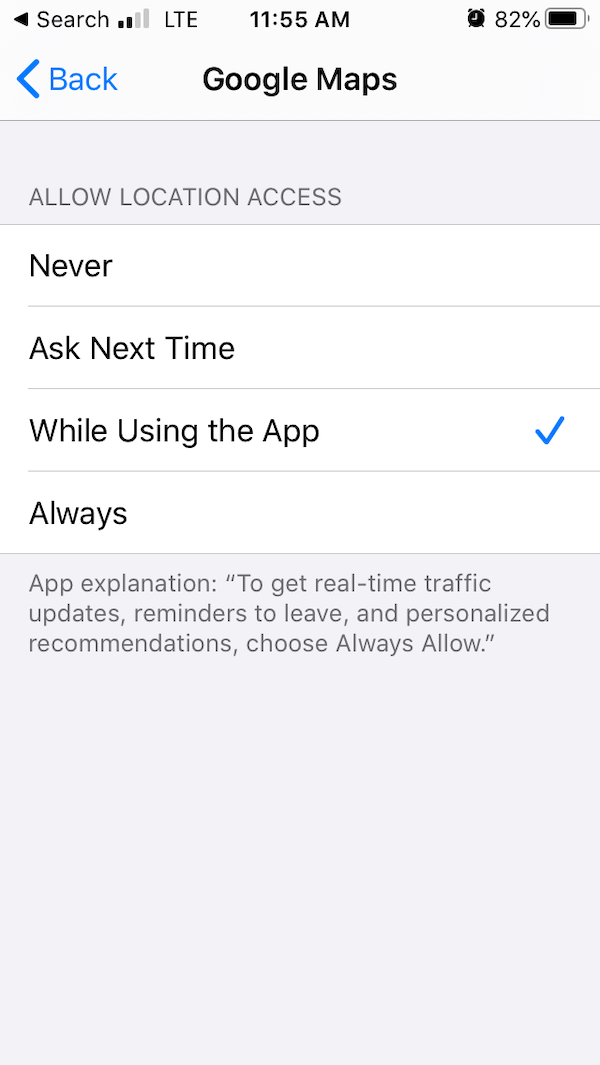 And yes, next time you use Google Maps, ask yourself, “does Google need to track where I am all of the time, or only while I’m actually navigating?”
And yes, next time you use Google Maps, ask yourself, “does Google need to track where I am all of the time, or only while I’m actually navigating?”
Search and Browsing
Many services use your search and browsing data to better personalize your experience. The downside of this convenience is that your search and browsing data can be quite private. Only you can decide where to draw the lines on this one, but understand that there are many options available to you including:
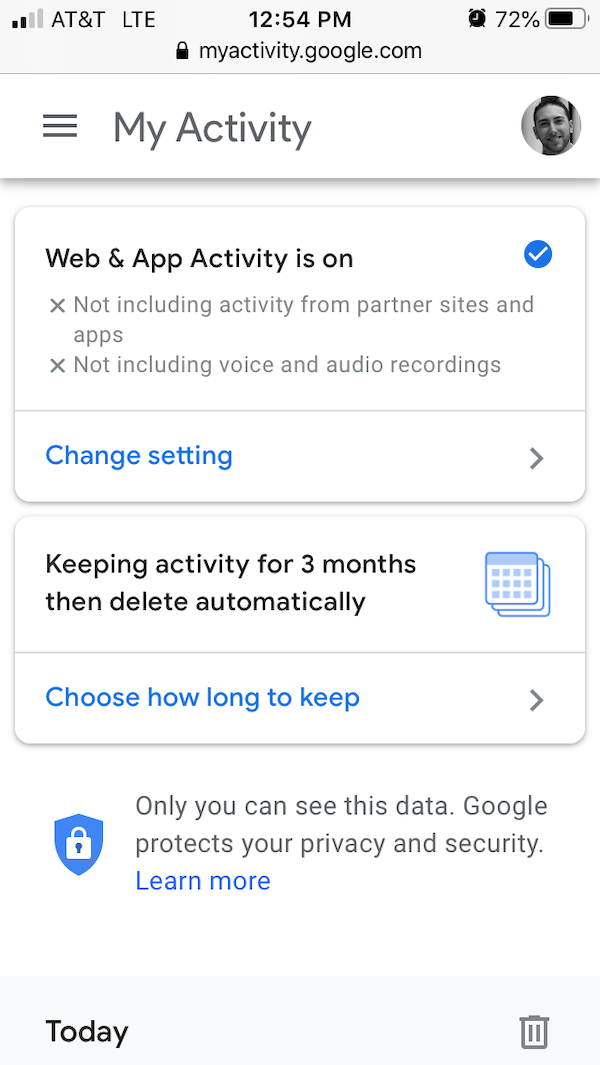
Limiting the amount of time your data is stored
This offers reasonable personalization with only moderate risk.
Choosing not to have your data stored at all
This offers no personalization, but with the least amount of risk.
Occasionally using incognito mode in conjunction with the suggestions above
This allows you to disassociate a particular search or session from the rest of your profile, which allows you to balance the benefits with the risk in real-time.
Offline
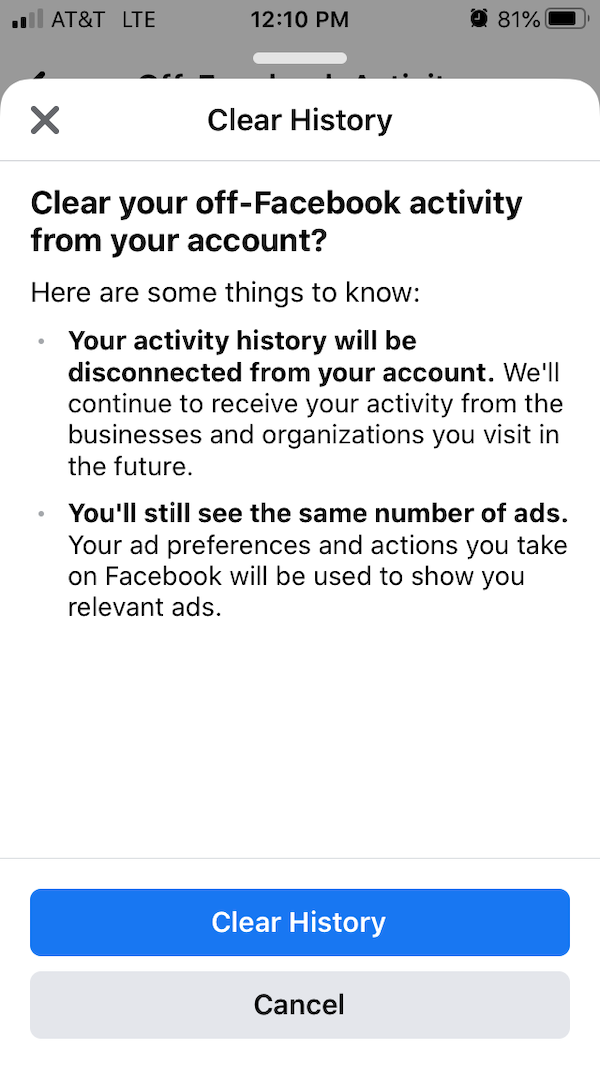
Perhaps the most revelatory invasion to privacy for most folks is the fact that some services pair up actions you take in the real world to the actions you take in the digital world, even if you do not have an app open or phone with you. For example, advertisers on Facebook are able to associate purchases you make using a credit card to your Facebook profile. This allows them to better track the effectiveness of their ad campaigns. This type of data pairing provides minimal benefit to you as a consumer but is wildly invasive to your privacy. Luckily, in most cases, you are in control of whether or not it happens. You just need to be diligent and state your preferences.
Obfuscate yourself
 Sometimes a company that you wish to engage with doesn’t give you any option but to provide it with data. In these cases, it’s often quite trivial to get around the privacy invasion as long as you’re sure that whatever is being asked is inconsequential to your engagement.
Sometimes a company that you wish to engage with doesn’t give you any option but to provide it with data. In these cases, it’s often quite trivial to get around the privacy invasion as long as you’re sure that whatever is being asked is inconsequential to your engagement.
- Use a throwaway mail service
- Fake your name, birthdate, address, etc
- Don’t provide any information that’s not strictly required
- Consider making certain purchases with virtual credit cards
Embrace unfettered encryption

For certain private messages and interactions, choosing the right product or tool can make a world of difference. The key here is favoring products that implement a very specific type of encryption. Let’s review:
- When information is encrypted in transit, it is virtually impossible for anyone without the encryption key to intercept the information as it travels from you up to a cloud service. Typically both you and the cloud service possess this key.
- When information is encrypted at rest, it is virtually impossible for anyone without the encryption key to read it from the cloud service. But if the cloud service possesses the key, then a third party (like the government) can compel it to produce the key and thus the information itself.
- When information is encrypted both in transit and at rest using an encryption key that only you possess, then it is virtually impossible for anyone but you to intercept or read the information. This is the only way to fully ensure that despite your use of a cloud service, your information will remain safe and private.
It’s easy to see why this matters. If you are sending private messages and wish to keep their contents totally private, you are much better off using services like Signal or Apple’s iMessage which are fully encrypted using a key that only you possess vs. services like Skype or Facebook Messenger which are encrypted in transit and at rest, but using a key that those respective services possess.
Secure your sign-ins

There will be cases where no matter how hard you try, you end up trusting certain services to process and store certain pieces of data. You are able to use the information above to make these decisions consciously, but you still need to take basic precautions to protect your accounts so that it’s not easy for hackers to compromise those accounts and get their hands on your data.
Use a password manager like 1Password. Password managers help you generate strong and unique passwords for each service and recall them every time you need to log in. They also help facilitate multi-factor authentication.
Case studies
In the last installment of this three-part series, I tie it all together by exploring a range of everyday behaviors in which many people engage - posting to Facebook, sending a text, making an online purchase, etc. This collection of case studies will provide you with a clear mental model for how to balance the convenience and connectivity of modern life with the privacy risks.